------------------------
Amiga Virus Encyclopedia
Joshua 2 Virus
------------------------
- Joshua2-Virus alternative names: Joshua3 or Switch-Off
Cold, BeginIO, ExecVec5
Has problems with a command in the C directory of WB1.3
Bootblock is now encrypted: loop: move.b (A0),D0
eori.b #$18,D0
The eor-byte changes and is located move.b D0,(A0)+
at position $3ff in the BB. Joshua2 cmpa.l A1,A0
can be recognized by the end of the bne loop
BB where X is changed according to the rts
eor-byte: .XX...XXX........XX.XX.XXXX...X.XX.
The dots can also be replaced by other characters.
Remark 17.07.93: Recently, an increase in infections of BBs
with Joshua2 has again been observed. Infecting an A600
(WITHOUT memoryexpansion) resulted in a GURU (because of Vec5),
but after a reset the virus was activated using COLD AND able
to spread!
---------------------------------------------------------
Translated to English by Dennis Boon © 2001 VHT-Denmark
Org. Test by Heiner Schneegold.
---------------------------------------------------------
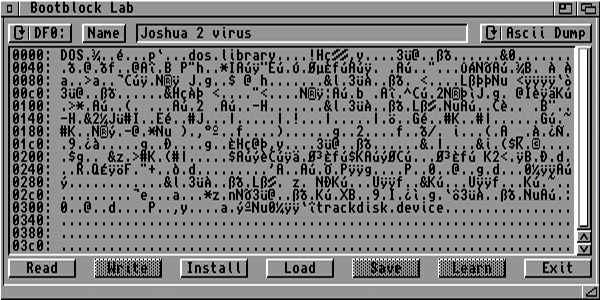
Ascii of Joshua 2 Bootblock virus:
|



