 |
Amiga Antivirus website |
 |
|
Index ☣ News ☣ Download ☣ Warnings ☣ Link ☣ Help ☣ Encyclopedia ☣ Unsorted ☣ Forum ☣ About ☣ FAQ ☣ Contact |
_________ _ ______ _____ _ ____ _
____/"""./###/____)\_____________ \ ./ ____/"""./____)\/""./______)\
/"""/ //_______ /"""/""./"___/_ \ // /""./ //""____/ //_______ \
/ / //"""/" / // / //____ \_ \/ / // // ____/ //"./""""/ //
\ // / ____/ / //""""/X\@!/ / // // /"""/ // ___/
\_____/\__/___/ ""\______/_________/ /___/____/\_____/\_____/\___/::....
/____/
VIRUS HELP TEAM
-------------------
For more information, contact us at:
www.vht-dk.dk
About Saddam Virus
------------------
IMPORTANT: 'Saddam' virus can only infect Amiga with Kickstart 1.2 or 1.3.
Please be very careful if you are working with the 'Saddam' file/link virus
Note that there is a boot virus with the same name don't be confused.
We still get a lot of reports about the world wide spreading of this very,
very nasty virus.
Here you have some facts about this virus:
1. The virus is a "multi-headed" file- and link virus. Always infected in
L/Dir, if there is not an L/Dir on the disk,it will make one by itself.
2. The Saddam file virus part is always to find in L/disk-validator, with
the same file length (1848) and of course.....the same name a diabolical
thing oh...boy..!
3. It can infect as the only one (we know), even if you have the new super
Fat Agnus (1MG ChipRam) and survive a reset. But remark the don't infect
if you have kickstart 2.0/3.0.
4. The Saddam link virus part is a VERY, VERY... easy spreading virus,
it will link to all files , e.g. to all executed, written or copied
files, but it does not change the file length,it only writes "IRAK" in
the start of the files. Please remark, that all these infected files
will cause Read /Write" errors! The original "Saddam" infects hard
disks too.
5. It is impossible to delete the virus or the link infected files with a
fileeditor like "Diskmaster", or from CLI
All wellknown antivirus program will find the 'Saddam' virus and make it
passive and repair the infected files very near 100%, but can't remove the
virus itself, you have to re-install the original Disk-vaildator.
----------------------------------------------------------------------------
Test of Saddan virus from the Virus Test Center in Hamburg:
===== Computer Virus Catalog 1.2: SADDAM file Virus (31-July-1993) =====
Entry...............: SADDAM_file Virus
Alias(es)...........: ---
Virus Strain........: SADDAM Virus Strain
Virus detected when.: ---
where.: ---
Classification......: File (!) variant of SADDAM virus, memory resident
Length of Virus.....: 1.Length on storage medium: 1848 byte
2.Length in RAM : 1936 byte
--------------------- Preconditions ------------------------------------
Operating System(s).: AMIGA-DOS
Version/Release.....: 1.2/all, 1.3/all
Computer model(s)...: All AMIGA models
--------------------- Attributes ---------------------------------------
Easy Identification.: A req.library is found with 1848 Bytes length.
Type of infection...: Self-identification method: virus searches for an
encryption-byte in req.library on disk that
its with its own.
System infection: virus replaces library called
"req.library" in libs:
Directory on inserted diskettes contain following
system routines/vectors (same as SADDAM virus):
System routines: - BeginIO(trackdisk.device)
- Close(trackdisk.device)
- InitResident(exec.library)
- OpenWindow(intuition.library)
System vectors: - ColdCapture(execbase)
- CoolCapture(execbase)
- KickTagptr(resident-struct.)
Infection Trigger...: 1) Opening req.library by exec function calls
2) OpenLibrary or OldOpenLibrary.
Storage media affected: Any floppy disk (every trackdisk.device)
Interrupts hooked...: Vertikal Blank interrupt works like a watchdog,
which guarantees that virus will stay in memory
(same as SADDAM virus).
Damage..............: Permanent damage:
1. If no req.library program exists on diskette
or no L: directory, both are built,replacing
req.library on disk.
2. Virus destroys a block by writing "LOOM"
over existing data.
3. Virus makes Bitmap NOT VALID, so running
Disk-Validator next time will infect System
(same as SADDAM).
4. Virus starts diskhead stepping in all floppy
drives and writing on disk (if writeable)
which will result in trackdisk errors
(same as SADDAM).
Transient damage: Mouse pointer will disappear,
and an Alert will be displayed with text:
"LOOOOM VIRUS". After pressing mouse
button, cold reset.
Damage Trigger......: Permanent damage:
1) insertion of a diskette
2) reading a Datablock
3) accessing rootblock
Transient damage: reading bootblock after a
certain time.
Particularities.....: 1) Virus uses direct Dos.Library Jumps.
2) Virus enrypts itself upon every infection with
another pseudo random number.
3) Virus installs a message port which is called
"mycon.write".
Similarities........: Similar to SADDAM LOOM Virus but as file infector;
other SADDAM variants are boot infectors.
--------------------- Agents -------------------------------------------
Countermeasures.....: VirusZ 3.06, VT 2.54, VirusChecker 6.28
Countermeasures successful: VirusZ 3.06, VT 2.54, VirusChecker 6.28
Standard means......: VT 2.54
--------------------- Acknowledgement ----------------------------------
Location............: Virus Test Center, University Hamburg, Germany
Classification by...: Jens Vogler
Documentation by....: Jens Vogler
Date................: 31-July-1993
Information Source..: Reverse analysis of virus code
===================== End of SADDAM file Virus =========================
More information:
A Disk-Validator-Virus is a special virus-type on the Amiga. To understand how
Disk-Validator-Viruses work, you have first to understand what a Disk-Validator
does: The Disk-Validator is a 1848 byte long executable file which has been
developed by Commodore itself. It is located in a directory called L on a disk,
or let's say expected by the AmigaOS in a directory called L, and has the
filename Disk-Validator (surprise :-)).
If you enter a disk which has been invalidated1 the AmigaOS will automatically
look for the Disk-Validator on this disk and loads and executes it automatically
if found. Then the program will correct the Rooblock so the disk is in a valid
state afterwards.
The Disk-Validator is not mandatory, this means that if a disk doesn't have this
file it just won't be loaded and the disk stays invalid (a requester will tell
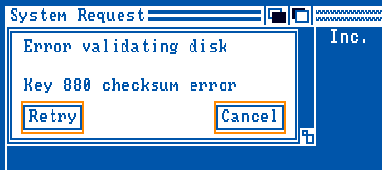
you that the disk is in an invalid state and you need to correct it):
      ![Screenshot of Saddam ][ Virus](../../desc/gif/DVII.gif) |
 |
Denmark & Canada Copyright © All Rights Reserved |
 |
 To cut a long story short:
* If a disk is in an invalid state the AmigaOS will look for a small program
called L:Disk-Validator
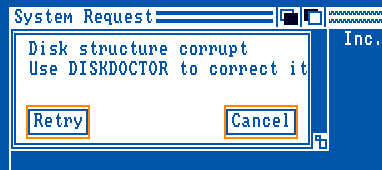
* If not found the AmigaDOS will pop-up a requester telling you that something is
wrong with the disk
* If found the program will be loaded an executed. Then the program will try to
solve the problem on the just inserted disk.
Disk-Validator Viruses take advantage of the AmigaOS automatism which loads and
executes this file by making the disk deliberately invalid2 and writing its virus
file as L:Disk-Validator on this disk. Next time you enter it the AmigaOS checks
if it is invalid. It is and therefore the AmigaOS loads and executes the program
Disk-Validator automatically but this time it is the virus itself!
The brilliant idea behind that is that the virus becomes active just by inserting
an infected disk. No need to start an infected file or booting with an infect
disks - even better: the AmigaOS itself becomes active and handles the execution
automatically.
The good news is that Disk-Validator-Viruses are only working on Amigas until
Kickstart 1.3 because in later Kickstart revisions (2.0, 3.0, 3.1 etc.) Commodore
integrated the Disk-Validator in the ROM, so there is no need to load the
Disk-Validator as a seperate applicaton anymore. If there is a Disk-Validator on
disk, it simply will be ignored.
To cut a long story short:
* If a disk is in an invalid state the AmigaOS will look for a small program
called L:Disk-Validator
* If not found the AmigaDOS will pop-up a requester telling you that something is
wrong with the disk
* If found the program will be loaded an executed. Then the program will try to
solve the problem on the just inserted disk.
Disk-Validator Viruses take advantage of the AmigaOS automatism which loads and
executes this file by making the disk deliberately invalid2 and writing its virus
file as L:Disk-Validator on this disk. Next time you enter it the AmigaOS checks
if it is invalid. It is and therefore the AmigaOS loads and executes the program
Disk-Validator automatically but this time it is the virus itself!
The brilliant idea behind that is that the virus becomes active just by inserting
an infected disk. No need to start an infected file or booting with an infect
disks - even better: the AmigaOS itself becomes active and handles the execution
automatically.
The good news is that Disk-Validator-Viruses are only working on Amigas until
Kickstart 1.3 because in later Kickstart revisions (2.0, 3.0, 3.1 etc.) Commodore
integrated the Disk-Validator in the ROM, so there is no need to load the
Disk-Validator as a seperate applicaton anymore. If there is a Disk-Validator on
disk, it simply will be ignored.